Understanding De-Identified Data: A Comprehensive Guide
In today's data-driven world, protecting sensitive information is crucial. De-identified data plays a vital role in achieving this, offering a way to analyze and utilize data while maintaining privacy and confidentiality. This guide will delve into the concept of de-identified data, exploring its definition, benefits, and practical applications.
What is De-Identified Data?

De-identified data refers to information that has been transformed to remove personally identifiable information (PII) or any elements that could potentially lead back to an individual. The primary goal is to protect privacy by making it extremely difficult, if not impossible, to associate the data with a specific person.
The process of de-identification involves removing or modifying direct identifiers (such as names, addresses, and social security numbers) and indirect identifiers (like birth dates, locations, and unique characteristics) from the dataset. This ensures that even if the data falls into the wrong hands, it cannot be used to identify or harm individuals.
Benefits of De-Identified Data

Privacy Protection

The most significant advantage of de-identified data is enhanced privacy protection. By removing personally identifiable information, organizations can analyze and share data without compromising the privacy and security of individuals. This is particularly crucial in sectors like healthcare, finance, and research, where sensitive data is routinely collected and processed.
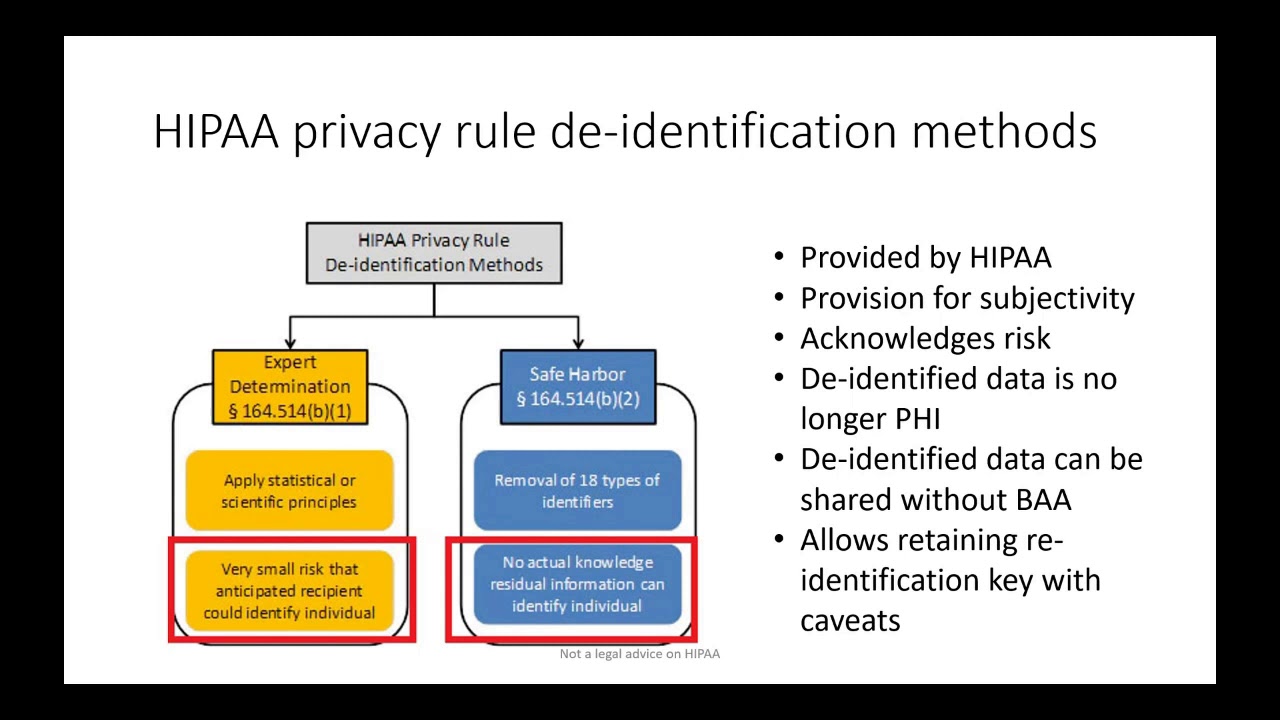
Compliance with Regulations

De-identification techniques are essential for complying with various data privacy regulations, such as the General Data Protection Regulation (GDPR) in the European Union and the Health Insurance Portability and Accountability Act (HIPAA) in the United States. These regulations mandate that organizations take steps to protect personal data, and de-identification is a key strategy to achieve this.
Data Sharing and Collaboration
De-identified data enables organizations to share information more freely, fostering collaboration and innovation. Researchers, analysts, and businesses can access and utilize de-identified datasets to gain valuable insights without the legal and ethical concerns associated with PII.
Methods of De-Identification

Anonymization
Anonymization is a process where all personally identifiable information is completely removed from the dataset. This method ensures that it is impossible to trace the data back to any individual. However, it may also result in the loss of valuable context and insights, as some information is stripped away.
Pseudonymization
Pseudonymization replaces direct identifiers with artificial identifiers or pseudonyms. For example, a person's name might be replaced with a unique code or ID. This method retains some indirect identifiers, which can be useful for maintaining data quality and facilitating re-identification if necessary. However, it is important to ensure that the pseudonyms cannot be easily reversed.
Generalization

Generalization involves replacing specific values with more general ones. For instance, instead of storing exact birth dates, the dataset might only include the year of birth. This technique reduces the risk of re-identification while preserving some level of detail.
Data Masking

Data masking, or data obfuscation, is a technique where sensitive data is hidden or replaced with fictitious information. This method ensures that the original data remains intact while providing a safe version for testing, training, or analysis. Data masking is often used in combination with other de-identification techniques.
Evaluating De-Identification Effectiveness

Assessing the effectiveness of de-identification is crucial to ensure that the data remains truly anonymous. Several methods are used to evaluate the risk of re-identification, including:
- K-Anonymity: This measure ensures that each record in the dataset is indistinguishable from at least K-1 other records regarding the quasi-identifiers (indirect identifiers). In simpler terms, it means that an individual's data cannot be distinguished from a group of K individuals.
- L-Diversity: L-Diversity focuses on the diversity of sensitive attributes within each group of K records. It ensures that even if an attacker knows the quasi-identifiers, they cannot easily infer sensitive information.
- T-Closeness: T-Closeness measures the similarity between the original dataset and the de-identified dataset. It aims to ensure that the de-identified data remains statistically close to the original, preventing any significant loss of information.
Practical Applications of De-Identified Data

Healthcare
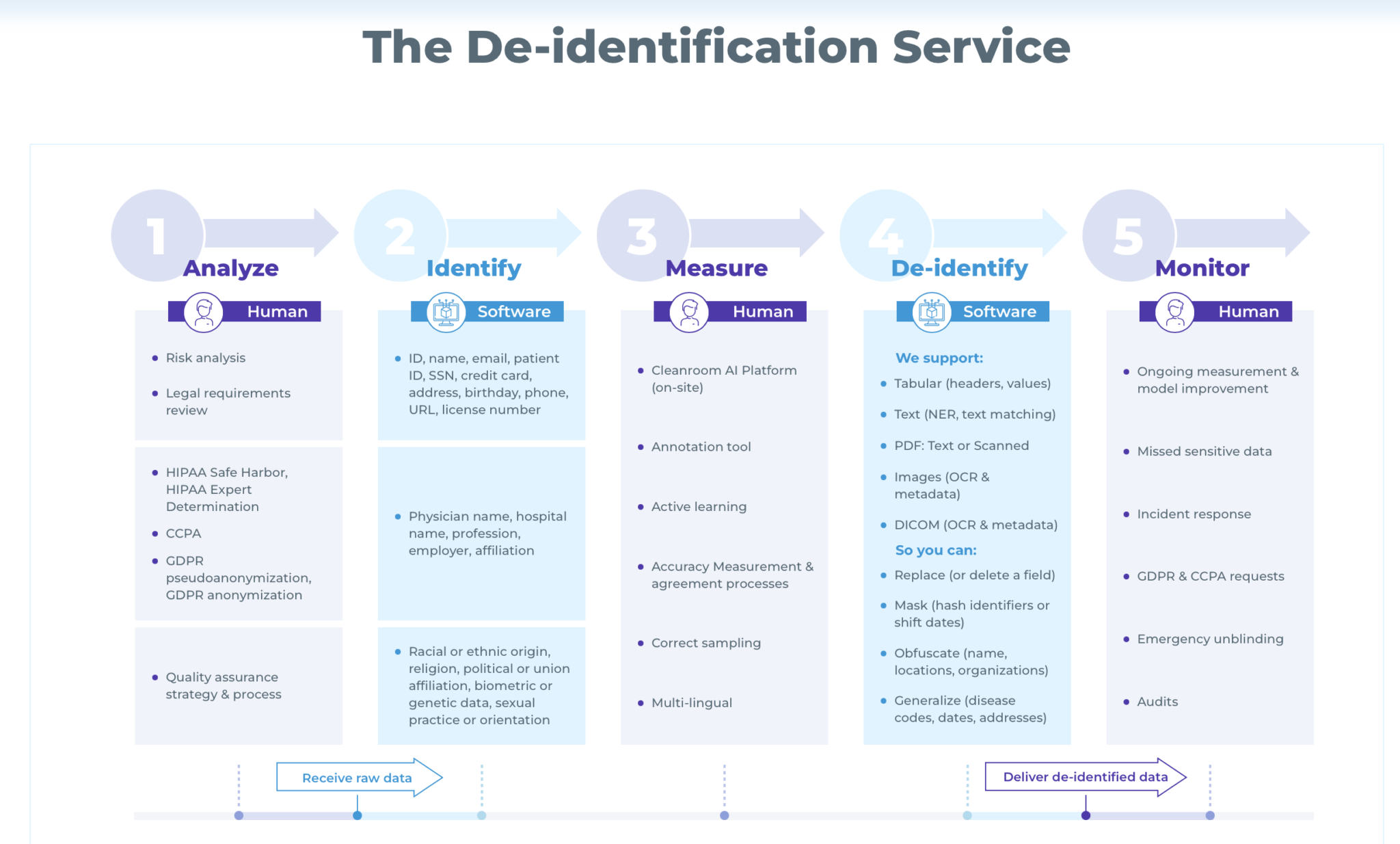
In the healthcare industry, de-identified data is crucial for medical research and improving patient care. By analyzing de-identified patient records, researchers can identify trends, develop new treatments, and enhance disease prevention strategies without compromising patient privacy.
Market Research

Market research companies often rely on de-identified data to gain insights into consumer behavior, preferences, and trends. This data helps businesses make informed decisions about product development, marketing strategies, and customer engagement.
Government and Public Sector

Governments and public sector organizations use de-identified data for various purposes, including policy development, urban planning, and resource allocation. By analyzing de-identified census data, for example, governments can make informed decisions about infrastructure projects and social services.
Challenges and Considerations

Data Quality
While de-identification aims to protect privacy, it can also impact data quality. Some de-identification techniques, such as generalization and data masking, may lead to a loss of granularity and detail, affecting the accuracy and usefulness of the data.
Re-Identification Risks
Despite the best efforts to de-identify data, there is always a risk of re-identification, especially with advanced data mining and linking techniques. Organizations must continuously assess and mitigate these risks to ensure the long-term effectiveness of their de-identification strategies.
Legal and Ethical Considerations
De-identification practices must align with legal and ethical guidelines. Organizations must ensure that they have the necessary consent or authorization to process and share de-identified data, especially when it involves sensitive information.
Conclusion
De-identified data is a powerful tool for organizations to unlock the value of their data while protecting privacy. By understanding the different de-identification techniques and their applications, businesses can make informed decisions about data handling and analysis. As data privacy regulations continue to evolve, the effective use of de-identified data will become even more critical for organizations across various industries.
What is the difference between anonymization and pseudonymization?
+
Anonymization completely removes all personally identifiable information, making it impossible to trace the data back to an individual. Pseudonymization, on the other hand, replaces direct identifiers with pseudonyms, allowing for potential re-identification if the pseudonyms are linked to other data sources.
Can de-identified data be used for machine learning and AI projects?
+
Yes, de-identified data is ideal for machine learning and AI projects as it allows for analysis and training without compromising individual privacy. However, it’s essential to ensure that the de-identification process is robust and that the data remains useful for the intended purposes.
Are there any limitations to de-identification techniques?
+
While de-identification techniques are powerful, they are not foolproof. Advanced data mining and linking techniques can potentially re-identify individuals, especially if multiple datasets are combined. Organizations must continuously assess and address these risks.